Steal the Key
Normally, hackers can break in by stealing unchanging digital certificates (similar to a key) that let them pose as trusted devices.
In a Fast-Moving World,
QWERX continuously verifies every machine on your network so attackers can’t turn them against you.
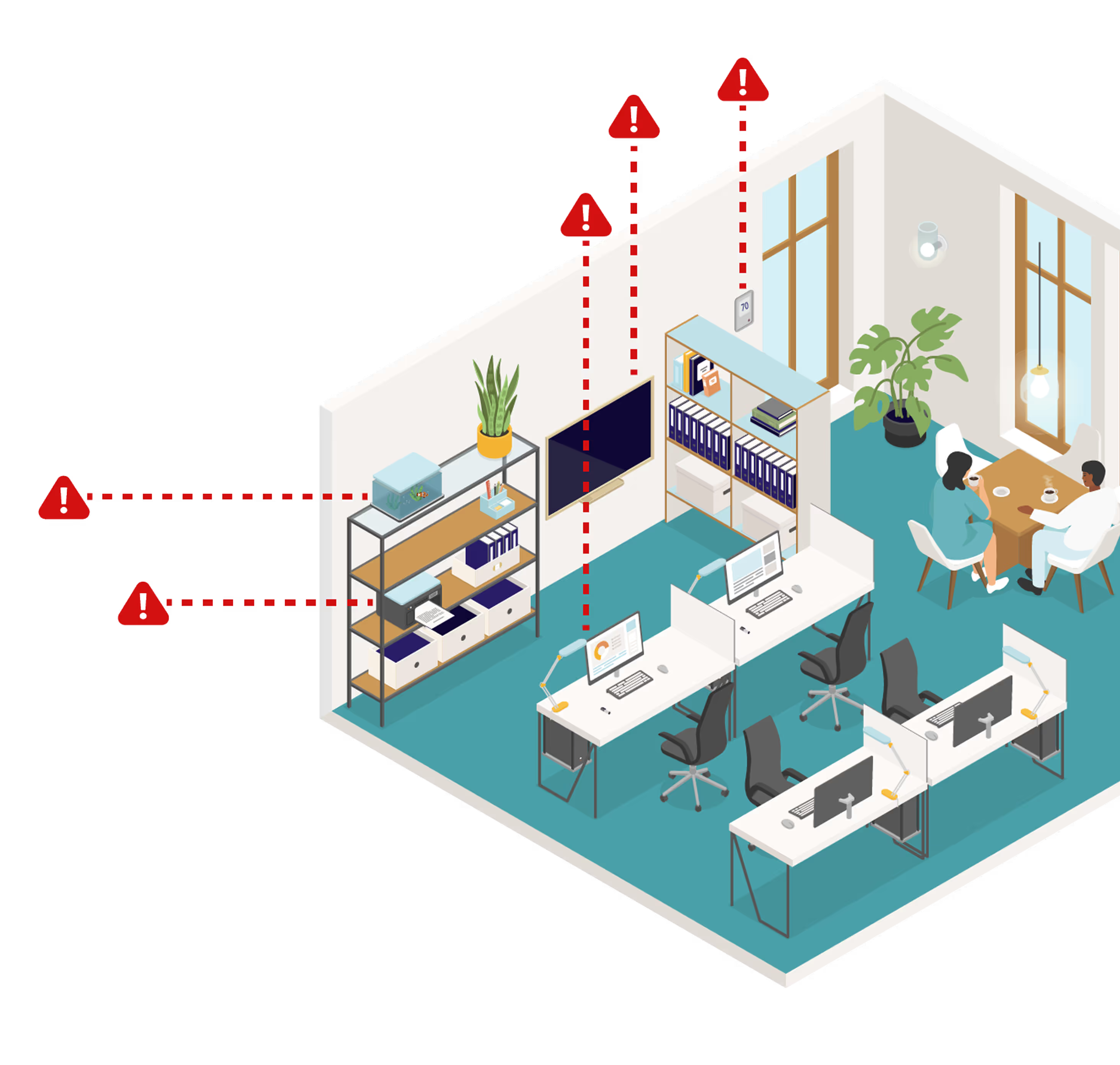
It’s overwhelming to secure each device… and just one weak spot can put your entire business at risk.
Thermostats
Smart TV’s
Fish tank tech
Printers
Check-in kiosks
Security cameras
Power grid sensors
Medical devices
Computers
...and more




Normally, hackers can break in by stealing unchanging digital certificates (similar to a key) that let them pose as trusted devices.
QWERX uses time against the attackers. We rotate the “key” every few seconds so that each one of your devices is continually verified.
By the time attackers try to use a “key,” the certificate has already changed. That means your devices stay verified and protected automatically with no extra work for your team.

We’ll show you the hidden threats across your devices.
QWERX continuously verifies each one in the background.
Your dashboard shows you every blocked attack.

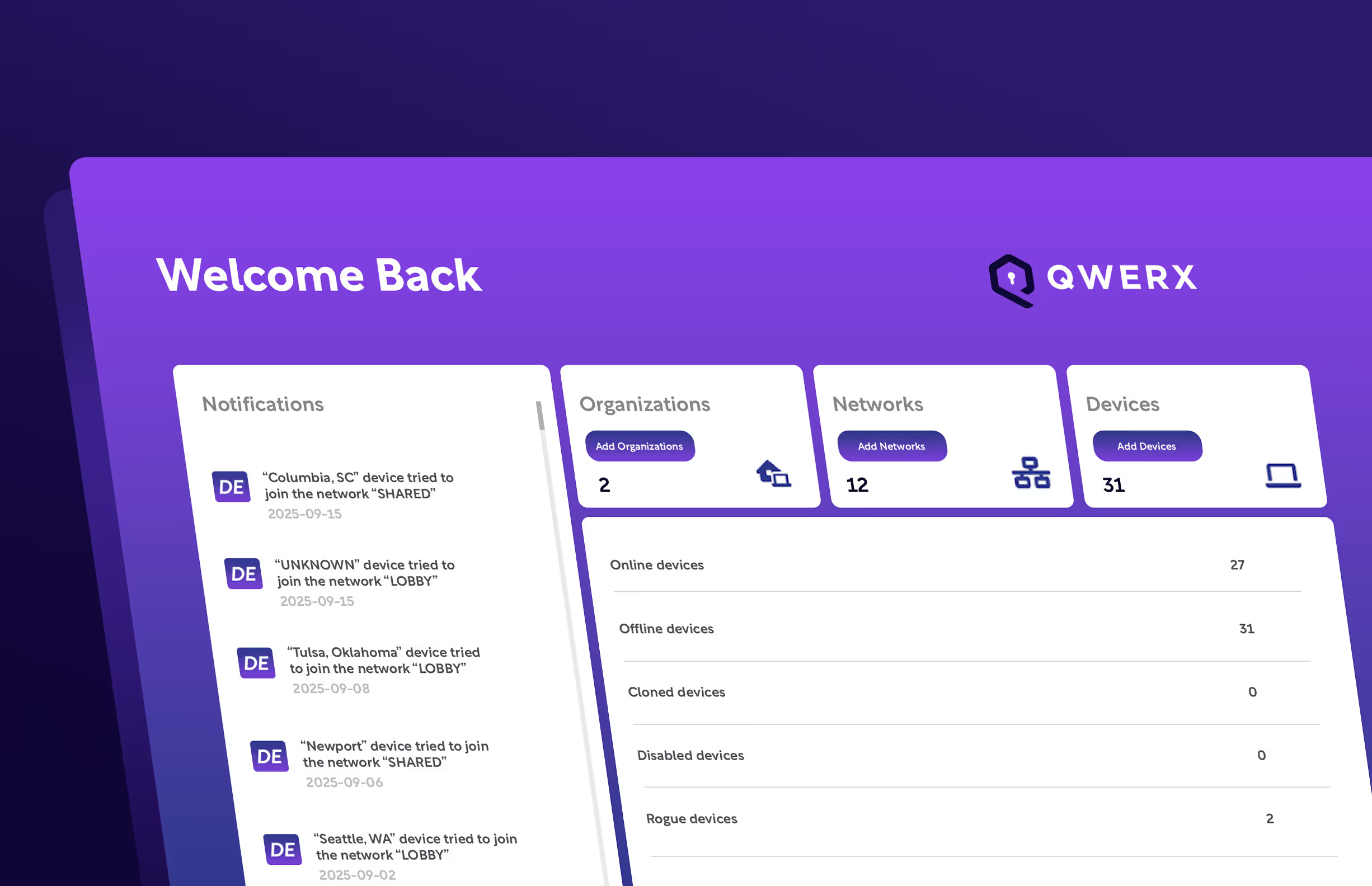
Your devices won’t be used against you. You can focus on growth instead of worrying about hackers.
Dashboard shows every attempted attack.
Feel in-control of your connected network.
Enroll or disconnect devices with just a few clicks.






As a cutting-edge healthcare informatics company, security is crucial to us. We needed a way to protect the employee health data that runs through our proprietary AI platform. One mistake would be catastrophic. QWERX made it simple, and now I don’t have to second-guess if we’re secure.
Rick, Align Admin CEO



